A strong KYC reduces uncertainty, not just risks.
KYC (Know Your Customer) is the process for identify and verify to the client or third party, understand who is dbehind (control/beneficiary), know the purpose of the relationship and apply continuous monitoring proportional to the risk.
Quick example (B2B)
A company opens an account or contracts a service. The KYC process doesn't end with the articles of incorporation: it also involves validating representatives, understanding the control structure, and documenting relevant findings to make consistent decisions.
KYC vs CDD vs EDD (to speak the same language):
- KYC: operational term, Know your customer, used on a daily basis.
- CDD (Customer Due Diligence): framework that includes identity, control, purpose, and monitoring.
- EDD (Enhanced Due Diligence): applies when the risk is greater and more depth and documentation are required.
KYC It's not just about asking for documents. It's an organized way to know who your company is dealing with, validate key data, and leave clear evidence of what was reviewed and how a decision was made. In this guide you will find simple concepts, step-by-step instructions, and common mistakes. common to apply it in Mexico without complicating the operation.
What is KYC in seconds (quick overview)
- KYC helps make decisions in an orderly manner: knowing who your company is related to and why a registration was approved (or not).
- The evidence andIt's part of the controlRecord what you consulted, when, what you found, and how it was resolved.
- Well done, saves time: reduces back-and-forth dealings with incomplete files and improves consistency during audits.
- It includes a checklist to standardize the process without making it bureaucratic.
Introduction
If your team needs register clients or third parties fast, but it must also meet controls of PLD/FT, It's normal to feel like KYC is a hindrance. In practice, the problem isn't KYC itself: it's that each department asks for different things, information is repeated, and the file becomes cluttered. incomplete.
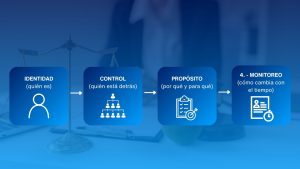
A well-designed KYC does the opposite: orders and accelerates. Define what data to request, what to validate, and how. classify risk and how leave evidence so that anyone (or an auditor) understands what was reviewed and why. In Mexico, this approach is related to AML/CFT practices and, in certain sectors, to specific obligations (for example, Vulnerable Activities under the LFPIORPI).
Related reading: Q-Suite (resources and webinars to strengthen compliance).
Key concepts
Beneficiary controller (why it matters):
Operational translation: If you only validate the company name but don't understand who controls or benefits from it, your risk assessment remains incomplete. The important thing is that the file explains how that control was determined, with evidence.
Lists in KYC: not all of them serve the same purpose.
To avoid confusion, separate by list type and document what was consulted, when, and what the resolution was.

Why it matters / Impact of not doing it
OperationTime and effort are wasted due to incomplete files and last-minute corrections; friction with the commercial area increases.
AuditControls without evidence (no log, date/time or documented resolution) are difficult to defend.
Risk managementTreating everyone the same causes the team to invest effort where it is not needed and arrive late to complex cases.
ReputationThird parties may question the consistency of its process and governance.
How to do it step by step
Key idea
- Each step must answer: to do y what to save as evidence.
- The goal is to have a process fast, repeatable y defensible.
Step 1. Define scope and policy
- Determine if it applies to customers, suppliers, candidates, or partners.
- Define roles, approvals, and timelines.
- Establish the order: high, relevant changes, and frequency.
Step 2. Standardize minimum data
- Use a single set of fields for natural and legal persons.
- Include representatives and powers where applicable.
- Avoid asking for "more than necessary": focus on usefulness and traceability.
Step 3. Identity verification (and documentation)
- Verify identities with reliable and independent sources, according to their policy.
- Record exceptions and who authorizes them.
Step 4. Identification of control/beneficiary
- Document ownership/control structure.
- Describe how you reached your conclusion and what evidence supports it.
Step 5. Searching and verifying lists (and resolving matches)
- Search lists by name and reasonable aliases.
- Define tie-breaking rules for false positives (e.g., date of birth, country, identifiers).
- Document the resolution and approval.
Step 6. Simple risk classification
- Use explainable criteria: industry, jurisdiction, complexity, product/service, and findings.
- Avoid "black box" models at the beginning.
Step 7. Periodic monitoring and updates
- Define frequency by risk level.
- It establishes triggers: changes in shareholders, representatives, business activity, country, or behavior.
Common mistakes and how to avoid them
- Each area requires different things.: Unify forms and define a minimum viable product per customer type.
- Requesting documents without understanding the profile: Connects data with purpose, activity, and expected profile.
- Do not validate representatives or signatoriesDefine clear rules for verifying authorization and identity.
- Do not document matches in lists: Keep evidence of the outcome and the resolution (who approved and why).
- Apply the same level of diligence to everyone: Uses a simplified Risk-Based Approach (RBA) at low risk and a reinforced approach at high risk.
- One-time KYC: Implements updates based on risk level and relevant events.
Next step: Review the scheme that best fits your operation.
Schedule a meeting with our team to receive professional support.
